- Cisco Asa Export Certificate Asdm
- Cisco Asa Export Identity Certificate Cli
- Cisco Asa Export Ca Certificate
- Cisco Asa Export Certificate
Use this guide to request an identity certificate from Cisco ASA.
If the keysize is largen than 2048 bits, the certificate can not be used for securing the the webssl/anyconnect. ASA currently does not support 4096 bit keys (Cisco bug ID CSCut53512) for SSL server authentication. However, IKEv2 does support the use of 4096 bit server certificates on the ASA 5580, 5585, and 5500-X platforms alone. Export to PDF Export to Word. Use this guide to request an identity certificate from Cisco ASA. Installing an identity certificate on the ASA using ADSM is not.
Installing an identity certificate on the ASA using ADSM is not complicated; however, there are specific details to know to avoid errors.
1. Have a Cisco ASA VPN and access to the ADSM admin console
1. Log into the Cisco admin console, and select Preferences under Tools
2. Check Preview commands before sending them to the device
This will enable review of the information that will be contained in the certificate before it is created
3. Click OK
4. In the admin console, select Remote Access VPN under Configuration, and expand the Certificate Management menu
5. Select Identity Certificates
2pac better dayz album download zip. 6. Click Add
7. Set the Trustpoint Name or leave as default
8. Select Add a new identity certificate
9. Select the Default RSA Key from the Key Pair dropdown, or click New.. to create a new one
For this configuration, the default key pair is selected
10. Click Select.. in the Certificate Subject DN section
11. Select Common Name (CN) from the Attribute dropdown, and set the Value to the Fully Qualified Domain Name (FQDN) of the Cisco ASA appliance
12. Click Add>>
13. Select Company Name (O) from the Attribute dropdown, and set the Value to the company's name
14. Click Add>>
15. Select Country (C) from the Attribute dropdown, and set the Value to US (or other if necessary)
16. Click Add>>
17. The new attributes and values should be present in the right-hand field
18. Click OK
19. The Certificate Subject DN field should now contain the attributes and values that were created in the previous steps
20. Click Advanced.. to ensure that the FQDN is correct
The FQDN may automatically be filled with the hostname and domain that are configured for the ASA
This field must match the Public Hostname (FQDN) that will be used by IPSec clients
Even if there are no initial plans to use IPSec, it is a best practice to install a certificate that will support certificate-authenticated IPSec clients
Without this field, IPSec clients cannot support certificate authentication, and the certificate would need to be replaced to enable support
21. Click Add Certificate
22. A preview window will appear, and ensure that the fqdn and subject-name are correct
23. Click Send if the configuration is correct, and an Identity Certificate Request window will appear
24. Choose a location in which to save the file, and click OK
25. In the Identity Certificates homepage, once a reply has been received, select the identity certificate and click Install
26. The Install Identity Certificate window will appear
27. Click Browse and locate the certificate file, and click Install Certificate
KB ID 0001091
Problem
Given the amount of ASA work I do it's surprising that the first time I saw an ASA 5506-X was last week (I've been working on larger firewalls for a while). I'm probably going to have to do a few of these over the next couple of years so I'll update this article as things surface.
Solution
Q: Can I just copy the config from an ASA 5505 to an ASA 5506-X?
A: No, that would be nice, truth be told if the 5505 is running an OS newer than 8.3, about 90% of the config can be copy/pasted if you know what you are doing.
The ASA 5506 Interfaces are different.
- Unlike its predecessor (and just about all other Cisco equipment), the interfaces start at number 1 (the 5505 starts at 0).
- The 5506 Interfaces are the opposite way round (left to right).
- The 5506 has IP addresses applied to its physical interfaces. Where as the 5505 had IP addresses applied to VLANs and then the physical interfaces were added to the appropriate VLAN. Note: the 5506 still supports VLANs, (5 or 30 with a security plus license).*
*UPDATE: After version 9.7 This has changed (on the 5506-X) See the following article for an explanation;
So let's say your 5505 has three interfaces called inside, outside, and DMZ, (yours might have different names, and you may only have two,) the relevant parts of the 5505 config would be;
VLAN Note: You might be wondering why no ports have been put into VLAN 1? By default all ports are in VLAN 1, So above, ports 0/1 and 0/3 to 0/7 are all in VLAN 1.
Outside IP Note: Yours may say ‘dhcp setroute' if it does not have a static IP , that's fine.
To convert that (Assuming you are NOT going to use the BVI interface, (see link above!);
AnyConnect Has Changed
If you use AnyConnect then prepare for a little hand wringing. The 5505 could support up to 25 SSLVPN connections. On a 5506 they are actually called AnyConnect now, and it supports up to 50.
There is no Essentials license for a 5506-X! Don't bother looking, you need to get your head into AnyConnect 4 licensing, I've already written about that at length.
Q: Does this mean I can't use my AnyConnect 3 (or earlier) packages in the new 5506?
A: Yes you can, but you will only get two connections, unless you purchase additional Apex/Plus licensing.
I'm working on the assumption that we are going to load in the AnyConnect 4 packages and use those. With that in mind if anyone manages to get them added to their Cisco profile without the ‘Additional Entitlement Required' then contact me, and let me know how, (link at bottom). I have to ring Cisco and use my employers partner status to get the client software 🙁
In addition to getting new AnyConnect Packages and loading them into the new 5506. If you have an anyconnect XML profile, that will also need copying into the new firewalls flash drive before you can paste the AnyConnect settings in.

Below you can see I've got a profile on my 5505.
AllMusic Review by Eduardo Rivadavia The Toy Dolls are all about fun, and their long-awaited full-length debut, 1982's Dig That Groove Baby, is an absolute punk gem. Bandleader Olga (aka Michael Algar) is capable of jaw-droppingly fast guitar picking, while lending his purposefully effeminate voice to. 5.0 out of 5 stars Best Oi Punk Album - Dig That Groove Baby, Glenda and the Test Tube Baby, Spiders in the Dressing Room, Stay Mellow. Reviewed in the United States on April 18, 2016. 5.0 out of 5 stars Best Oi Punk Album - Dig That Groove Baby, Glenda and the Test Tube Baby, Spiders in the Dressing Room, Stay Mellow Reviewed in the United States on April 18, 2016 The Toy Dolls are one of my all time favorite punk bands. 'and their full-length debut, 1982's Dig.
Tools > File Transfer > File Transfer > Between Local PC and Flash. (Do the reverse to get the file(s) into the new 5506).
Note: You can also do this from CLI by copying the file to a TFTP server.
Below is a typical AnyConnect config from an ASA 5505, I've highlighted the lines that will cause you problems.
ASA Transferring Certificates From One ASA to Another
Cisco Asa Export Certificate Asdm
I appreciate a lot of you wont be using certificates, and even if you use AnyConnect you just put up with the certificate error. That's fine, but do me a favor? Before you do anything else go and generate the RSA keys on your new 5506 before you do anything else, (people forgetting to do this has cause me a LOT of grief over the years). So set the host name, domain-name, and then generate the keys like so;
OK, so if you are still reading this section, then you have at least one certificate, that you need to move to the new firewall. For each scenario here's what I recommend you do;
Self Signed Certificate from your own PKI / CA Server : Just generate a new cert for the new firewall and import it the same as you did on the old firewall
Externally / Publicly signed certificate that you have paid for: This we will need to export then import onto the new 5506. (Note: If there's not much time left to run on the validity, it may be easier to get onto the certificate vendor and have a new one reissued to save you having to replace it in a couple of months – just a thought).
If you have purchased a certificate you will have already gone though the process below;
The easiest option for you is to go where you purchased the cert, download it again, and import it into the new firewall. But here's where you find out you forgot the username and password you used, or the guy who sorted this out has left the company etc. If that is the case all is not lost. You can export an identity certificate, either from the ADSM;
Cisco ASA Export Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Select the certificate > Export > Choose a location and a ‘pass-phrase'.
Cisco ASA Export Certificates From Command Line.
To do the same at CLI the procedure is as follows;
Cisco ASA Import Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Add > Use the same Trustpoint name as the source firewall > Browse the file you exported earlier > Enter the passphrase > Add Certificate.
Cisco ASA Import Certificates From Command Line.
To do the same at CLI the procedure is as follows, Note: You need to paste in the text from the output.
Assorted Firewall Migration ‘Gotchas'
Time (Clock Setting)
If you do any AAA via Kerberos or LDAP, then not having the time correct on the new ASA might get you locked out of it. I would always suggest setting up NTP so do that before you restart.
ARP Cache
Not on the ASA, but on the devices the ASA is connecting to, (routers and switches etc). Unplug an ASA 5505 and plug in an ASA 5506, and nine times out of ten you will not get comms. This is because the device you are connecting to has cached the MAC address of the old firewall in its ARP cache. So either reboot the device, (or it thats not practical, lower the ARP cache to about 30 seconds).
ASA 5505 to 5506 Config To Copy And Paste
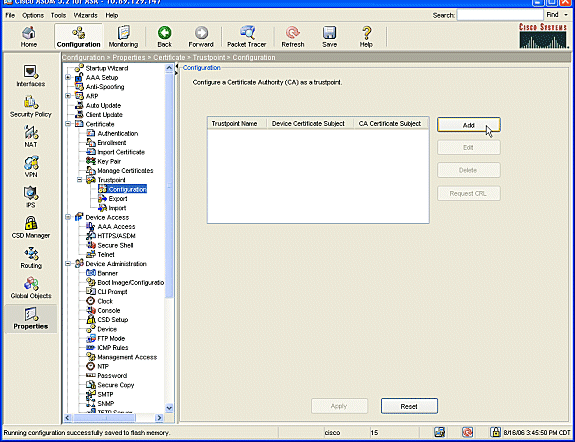
11. Select Common Name (CN) from the Attribute dropdown, and set the Value to the Fully Qualified Domain Name (FQDN) of the Cisco ASA appliance
12. Click Add>>
13. Select Company Name (O) from the Attribute dropdown, and set the Value to the company's name
14. Click Add>>
15. Select Country (C) from the Attribute dropdown, and set the Value to US (or other if necessary)
16. Click Add>>
17. The new attributes and values should be present in the right-hand field
18. Click OK
19. The Certificate Subject DN field should now contain the attributes and values that were created in the previous steps
20. Click Advanced.. to ensure that the FQDN is correct
The FQDN may automatically be filled with the hostname and domain that are configured for the ASA
This field must match the Public Hostname (FQDN) that will be used by IPSec clients
Even if there are no initial plans to use IPSec, it is a best practice to install a certificate that will support certificate-authenticated IPSec clients
Without this field, IPSec clients cannot support certificate authentication, and the certificate would need to be replaced to enable support
21. Click Add Certificate
22. A preview window will appear, and ensure that the fqdn and subject-name are correct
23. Click Send if the configuration is correct, and an Identity Certificate Request window will appear
24. Choose a location in which to save the file, and click OK
25. In the Identity Certificates homepage, once a reply has been received, select the identity certificate and click Install
26. The Install Identity Certificate window will appear
27. Click Browse and locate the certificate file, and click Install Certificate
KB ID 0001091
Problem
Given the amount of ASA work I do it's surprising that the first time I saw an ASA 5506-X was last week (I've been working on larger firewalls for a while). I'm probably going to have to do a few of these over the next couple of years so I'll update this article as things surface.
Solution
Q: Can I just copy the config from an ASA 5505 to an ASA 5506-X?
A: No, that would be nice, truth be told if the 5505 is running an OS newer than 8.3, about 90% of the config can be copy/pasted if you know what you are doing.
The ASA 5506 Interfaces are different.
- Unlike its predecessor (and just about all other Cisco equipment), the interfaces start at number 1 (the 5505 starts at 0).
- The 5506 Interfaces are the opposite way round (left to right).
- The 5506 has IP addresses applied to its physical interfaces. Where as the 5505 had IP addresses applied to VLANs and then the physical interfaces were added to the appropriate VLAN. Note: the 5506 still supports VLANs, (5 or 30 with a security plus license).*
*UPDATE: After version 9.7 This has changed (on the 5506-X) See the following article for an explanation;
So let's say your 5505 has three interfaces called inside, outside, and DMZ, (yours might have different names, and you may only have two,) the relevant parts of the 5505 config would be;
VLAN Note: You might be wondering why no ports have been put into VLAN 1? By default all ports are in VLAN 1, So above, ports 0/1 and 0/3 to 0/7 are all in VLAN 1.
Outside IP Note: Yours may say ‘dhcp setroute' if it does not have a static IP , that's fine.
To convert that (Assuming you are NOT going to use the BVI interface, (see link above!);
AnyConnect Has Changed
If you use AnyConnect then prepare for a little hand wringing. The 5505 could support up to 25 SSLVPN connections. On a 5506 they are actually called AnyConnect now, and it supports up to 50.
There is no Essentials license for a 5506-X! Don't bother looking, you need to get your head into AnyConnect 4 licensing, I've already written about that at length.
Q: Does this mean I can't use my AnyConnect 3 (or earlier) packages in the new 5506?
A: Yes you can, but you will only get two connections, unless you purchase additional Apex/Plus licensing.
I'm working on the assumption that we are going to load in the AnyConnect 4 packages and use those. With that in mind if anyone manages to get them added to their Cisco profile without the ‘Additional Entitlement Required' then contact me, and let me know how, (link at bottom). I have to ring Cisco and use my employers partner status to get the client software 🙁
In addition to getting new AnyConnect Packages and loading them into the new 5506. If you have an anyconnect XML profile, that will also need copying into the new firewalls flash drive before you can paste the AnyConnect settings in.
Below you can see I've got a profile on my 5505.
AllMusic Review by Eduardo Rivadavia The Toy Dolls are all about fun, and their long-awaited full-length debut, 1982's Dig That Groove Baby, is an absolute punk gem. Bandleader Olga (aka Michael Algar) is capable of jaw-droppingly fast guitar picking, while lending his purposefully effeminate voice to. 5.0 out of 5 stars Best Oi Punk Album - Dig That Groove Baby, Glenda and the Test Tube Baby, Spiders in the Dressing Room, Stay Mellow. Reviewed in the United States on April 18, 2016. 5.0 out of 5 stars Best Oi Punk Album - Dig That Groove Baby, Glenda and the Test Tube Baby, Spiders in the Dressing Room, Stay Mellow Reviewed in the United States on April 18, 2016 The Toy Dolls are one of my all time favorite punk bands. 'and their full-length debut, 1982's Dig.
Tools > File Transfer > File Transfer > Between Local PC and Flash. (Do the reverse to get the file(s) into the new 5506).
Note: You can also do this from CLI by copying the file to a TFTP server.
Below is a typical AnyConnect config from an ASA 5505, I've highlighted the lines that will cause you problems.
ASA Transferring Certificates From One ASA to Another
Cisco Asa Export Certificate Asdm
I appreciate a lot of you wont be using certificates, and even if you use AnyConnect you just put up with the certificate error. That's fine, but do me a favor? Before you do anything else go and generate the RSA keys on your new 5506 before you do anything else, (people forgetting to do this has cause me a LOT of grief over the years). So set the host name, domain-name, and then generate the keys like so;
OK, so if you are still reading this section, then you have at least one certificate, that you need to move to the new firewall. For each scenario here's what I recommend you do;
Self Signed Certificate from your own PKI / CA Server : Just generate a new cert for the new firewall and import it the same as you did on the old firewall
Externally / Publicly signed certificate that you have paid for: This we will need to export then import onto the new 5506. (Note: If there's not much time left to run on the validity, it may be easier to get onto the certificate vendor and have a new one reissued to save you having to replace it in a couple of months – just a thought).
If you have purchased a certificate you will have already gone though the process below;
The easiest option for you is to go where you purchased the cert, download it again, and import it into the new firewall. But here's where you find out you forgot the username and password you used, or the guy who sorted this out has left the company etc. If that is the case all is not lost. You can export an identity certificate, either from the ADSM;
Cisco ASA Export Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Select the certificate > Export > Choose a location and a ‘pass-phrase'.
Cisco ASA Export Certificates From Command Line.
To do the same at CLI the procedure is as follows;
Cisco ASA Import Certificates From ASDM
Configuration > Device Management > Certificate Management > Identity Certificates > Add > Use the same Trustpoint name as the source firewall > Browse the file you exported earlier > Enter the passphrase > Add Certificate.
Cisco ASA Import Certificates From Command Line.
To do the same at CLI the procedure is as follows, Note: You need to paste in the text from the output.
Assorted Firewall Migration ‘Gotchas'
Time (Clock Setting)
If you do any AAA via Kerberos or LDAP, then not having the time correct on the new ASA might get you locked out of it. I would always suggest setting up NTP so do that before you restart.
ARP Cache
Not on the ASA, but on the devices the ASA is connecting to, (routers and switches etc). Unplug an ASA 5505 and plug in an ASA 5506, and nine times out of ten you will not get comms. This is because the device you are connecting to has cached the MAC address of the old firewall in its ARP cache. So either reboot the device, (or it thats not practical, lower the ARP cache to about 30 seconds).
ASA 5505 to 5506 Config To Copy And Paste
Cisco Asa Export Identity Certificate Cli
Below I'll put a full config for an ASA 5505. If the text is normal,the commands can be copy and pasted directly into the new firewall. If the text is RED, then you can NOT, and I will have outlined the problems above.
Cisco Asa Export Ca Certificate
Related Articles, References, Credits, or External Links
Cisco Asa Export Certificate
NA
